Apache Struts is one of the most widely used open source frameworks for developing Java-based web applications. Thousands of enterprises around the world, including Fortune 100 companies and the U.S Internal Revenue Service (IRS), use this popular framework in their applications.
Despite going mainstream in software development, Apache Struts has had a rough history of security issues over the years. If you perform a basic search on MITRE, you will find 79 CVE entries (at the time of writing) related to Apache struts.
Research by WhiteSource on the top six vulnerable open source projects ranked Apache struts second only behind Apache Tomcat, among the most weaponized frameworks.
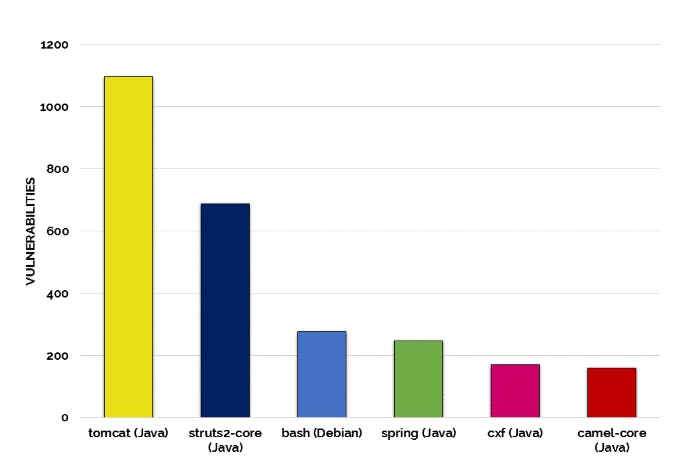 Most vulnerable projects - WhiteSource
Most vulnerable projects - WhiteSource
This post is designed to walk you through common Apache Struts vulnerabilities, assess their impact, and provide actionable tips on how you can mitigate them.
An Insight Into Apache Struts Vulnerabilities
Most security vulnerabilities in Apache Struts and other development frameworks involve data coming from untrusted sources. For instance, maliciously crafted user input is way too dangerous because it provides a basis for attacks through SQL queries, deserialization, and other interpreted languages.
In Apache Struts, the Object-Graph Navigation Language (OGNL) is the expression language used to handle Java objects. An attacker can successfully inject a custom namespace or input parameters in OGNL expressions to allow arbitrary remote code execution (RCE).
The OGNL expression injection, one of the most common techniques for exploiting Apache Struts, works in a very similar way to Server-Side Template Injection (SSTI).
Over the years, Apache Struts has suffered a number of vulnerabilities for failing to sufficiently validate data in user-supplied fields before passing OGNL expressions to internal functions. This was the kind of issue behind two related high-risk Apache Struts vulnerabilities, CVE-2016-4438 and CVE-2016-3081.
In the code snippet below, methods implemented in the Struts framework i.e getMethod(), getActionName(), and getNamespace() can potentially return untrusted user input.
String methodName = proxy.getMethod(); //<--- untrusted source,
LOG.debug("Executing action method = {}", methodName);
String timerKey = "invokeAction: " + proxy.getActionName();
try {
UtilTimerStack.push(timerKey);
Object methodResult;
try {
//Possible Remote Code Execution ----->
methodResult = ognlUtil.getValue(methodName + "()", getStack().getContext(), action);
When untrusted remote input is passed as an argument via the variable methodName to the method OgnlUtil::getValue(), an attacker could successfully execute arbitrary code.
Another remote code execution vulnerability on Apache Struts is CVE 2017-11778. This vulnerability is triggered on servers running Struts when an attacker injects maliciously crafted input as a parameter in HTTP requests.
It is evident that there are a series of RCE vulnerabilities related to insufficient input validation within a particular functional area of the Apache Struts code. These are easier to fix because developers with knowledge in that functional area can quickly identify and resolve the vulnerability without introducing new issues.
However, there are other vulnerabilities that operate far deeper within the code and libraries used by Struts. CVE-2018-11776, one of the latest Apache Struts vulnerabilities, is a good example of CVEs that operate at such a deep level.
RCE vulnerabilities on Apache Struts pose a significant risk to organizations and end-users, especially if unauthenticated attackers can successfully exploit the vulnerability. In such a case, a vulnerability has dire consequences, such as allowing the adversary to run arbitrary programs, access data from the database, or even retrieve the application's source code.
Case in Point: The Equifax Data Breach
Equifax, a leading consumer reporting credit agency in the U.S., suffered a massive data breach in 2017 when it failed to identify and patch a security loophole in Apache Struts. The vulnerability, CVE-2017-9805, was a result of incorrect exception handling and generation of error messages during file upload in the Jakarta Multipart parser.
CVE-2017-9805 allowed arbitrary remote code execution via specially crafted content-disposition, content-type or content-type HTTP header that contains a [#cmd]) = string. Hackers capitalized on this vulnerability to compromise Equifax in a breach that exposed over 148 million U.S. customers' information that included names, social security numbers, addresses, birth dates, and some driver licenses.
The Equifax data breach also lifted credit card details for over 209,000 consumers and over 182,000 credit dispute documents containing personal information. The impact of the attack was felt beyond the U.S, affecting over 15.2 million U.K customers and 19,000 Canadian residents.
As you can see, vulnerabilities in Apache Struts or any other development framework pose great security risks, not only to enterprises but also to consumers. It is therefore vital for developers to stay on top of their application security.
Addressing Apache Struts Vulnerabilities
As modern software becomes increasingly complex, so does the risk of introducing security issues in an application increase. Development teams should therefore focus on securing every bit of data that passes the application.
This starts by embracing secure development practices such as proper input validation and sanitization, whether on the client-side or server-side Most vulnerabilities in Apache Struts can be exploited using maliciously crafted user input.
As a rule of thumb, always treat user input as untrusted before using it in your application.
Another step for securing projects or applications using the Apache Struts framework is by timely identification and remediation of potential security issues. This can be achieved by scanning your codebase for known open source vulnerabilities.
So, if you use Apache Struts or rely on third-party integrations that uses this framework, consider using a tool like WhiteSource Bolt to automatically check your projects for security vulnerabilities.
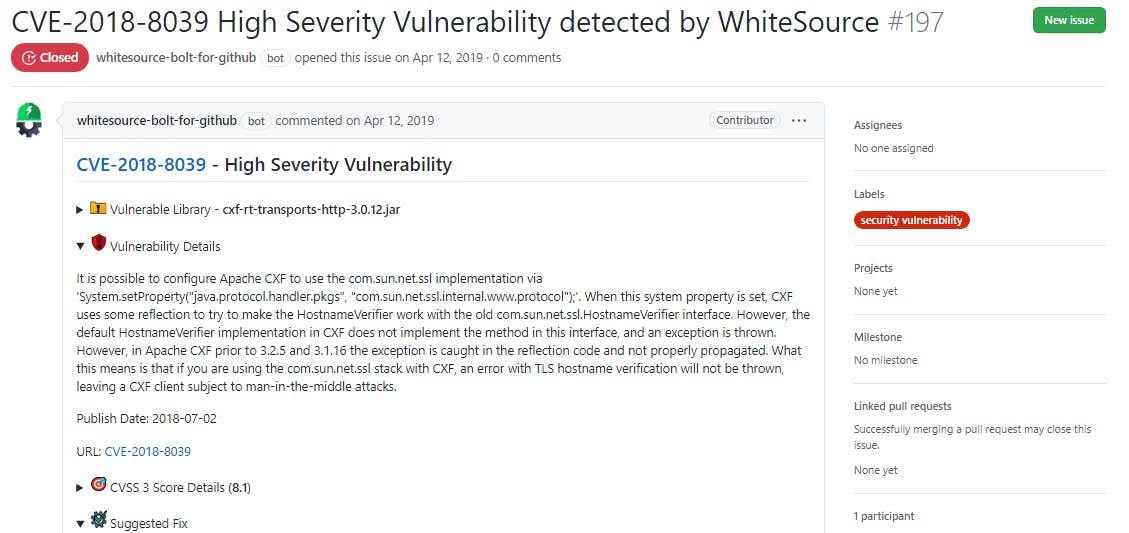 WhiteSource Bolt detects Apache vulnerabilities
WhiteSource Bolt detects Apache vulnerabilities
WhiteSource Bolt will scan your codebase, notifies you on the vulnerable libraries with detailed information that includes versions affected and the CVSS Score. It also suggests a fix for easier remediation of the vulnerability.
While continuous monitoring and fixing of vulnerabilities are important, the following steps can help Apache Struts users mitigate common vulnerabilities:
- Verify that no unauthorized modifications in the system occurred before patching the application.
- Use the latest version of the Apache Struts framework in your application.
- Apply the principle of least privilege across all services in your application
- Remind end-users not to follow links or visit website form untrusted or unknown sources
Even if Apache Struts is prone to critical security vulnerabilities, it is almost impossible to ditch such a widely-used framework at the enterprise level. So, use the above tips to keep your Struts application security in top shape!

